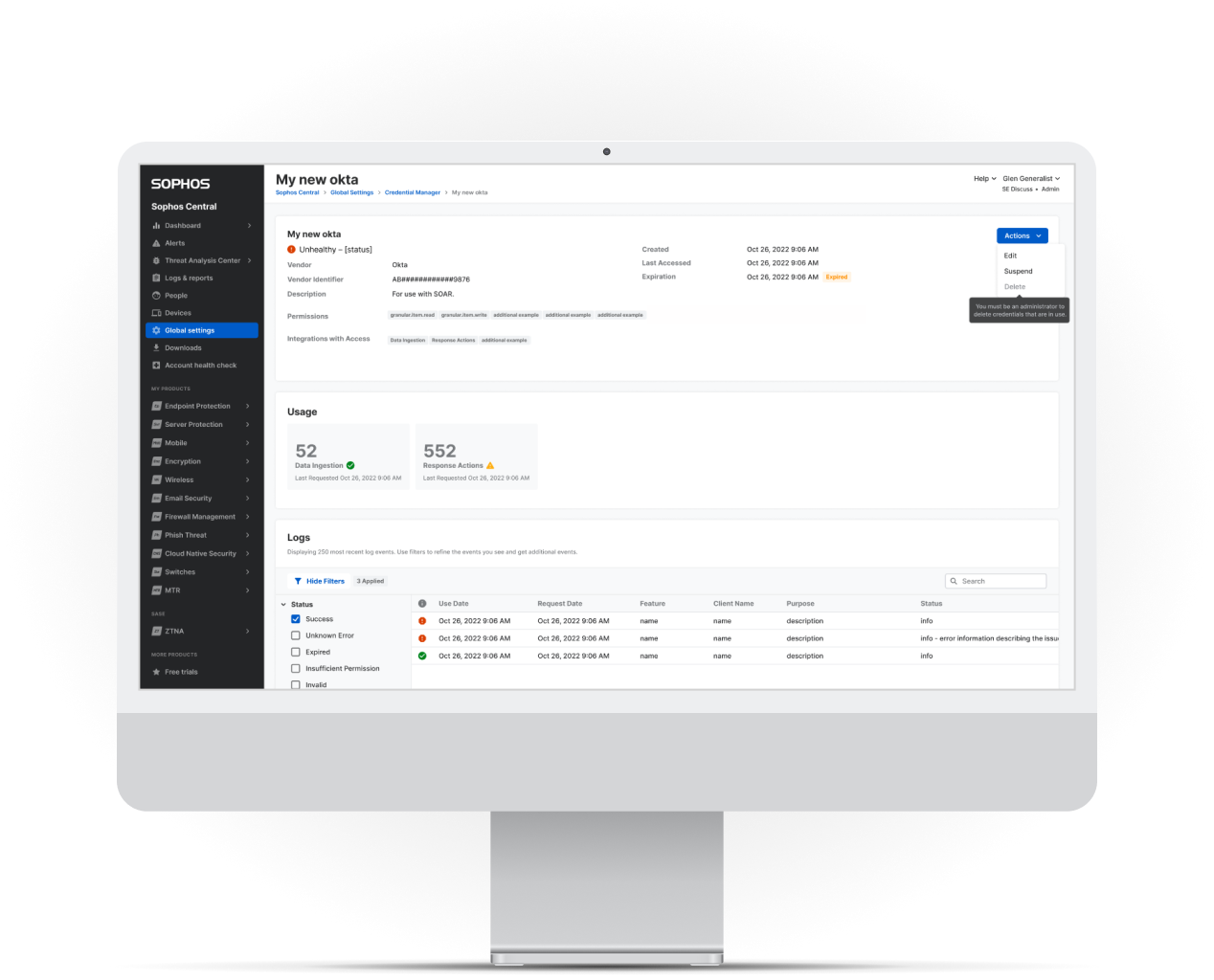
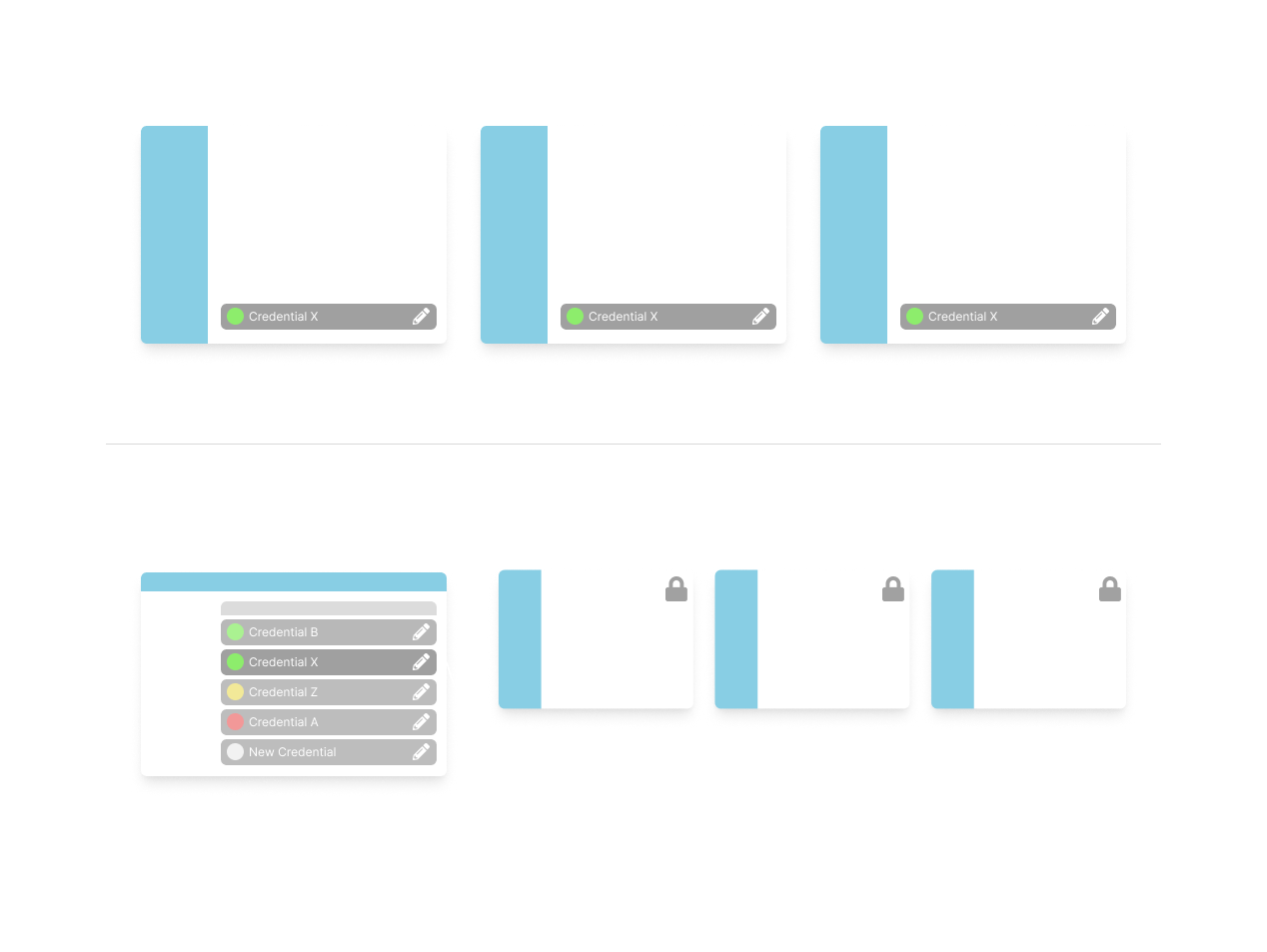
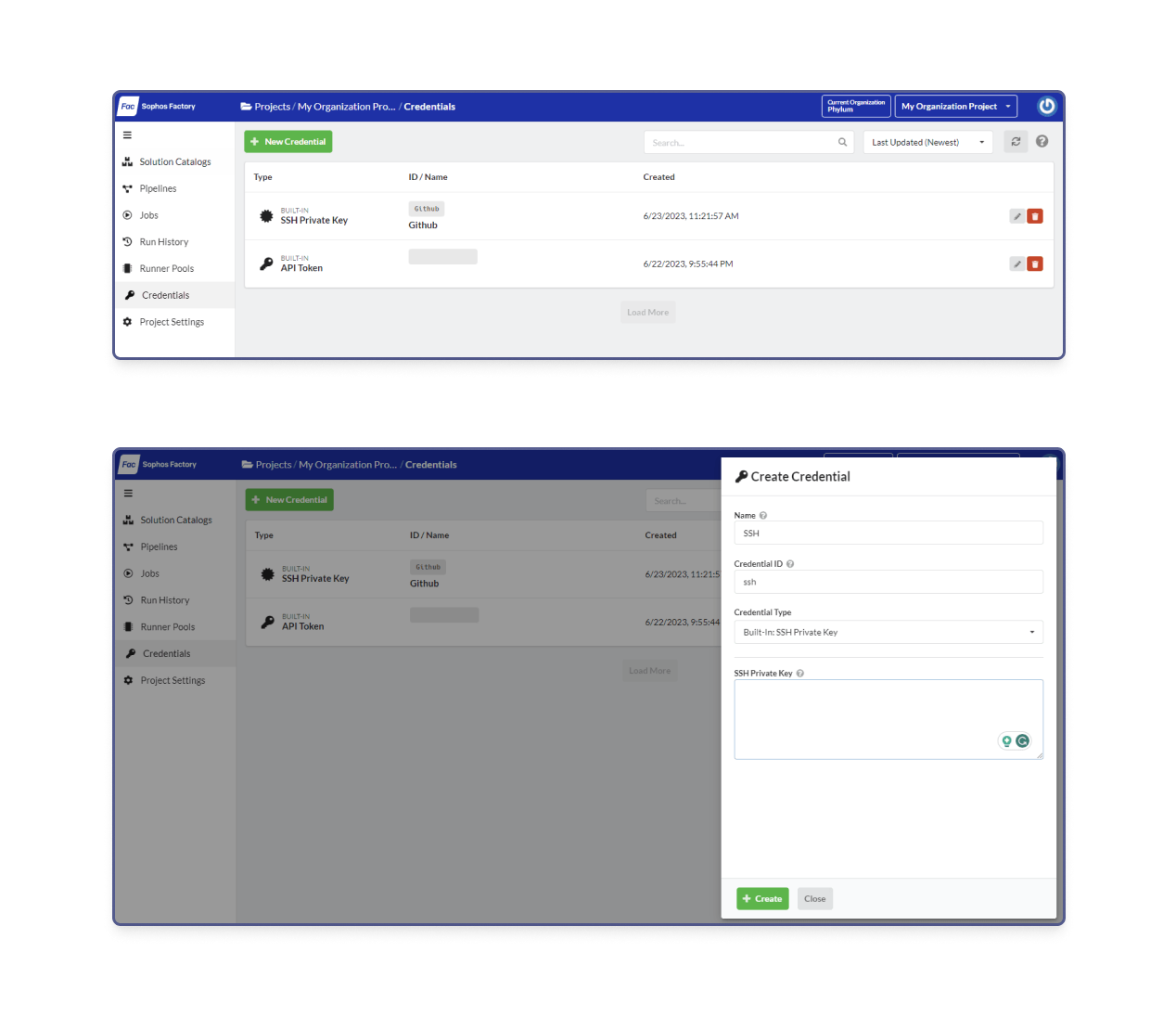
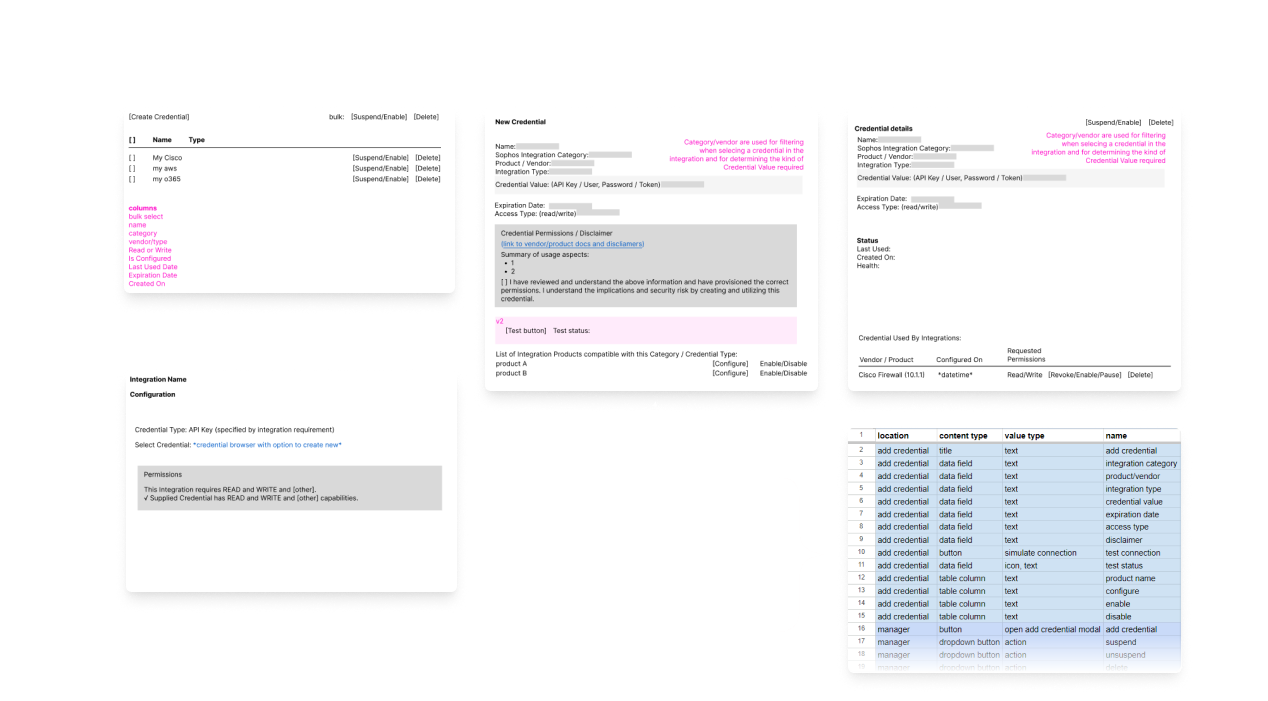
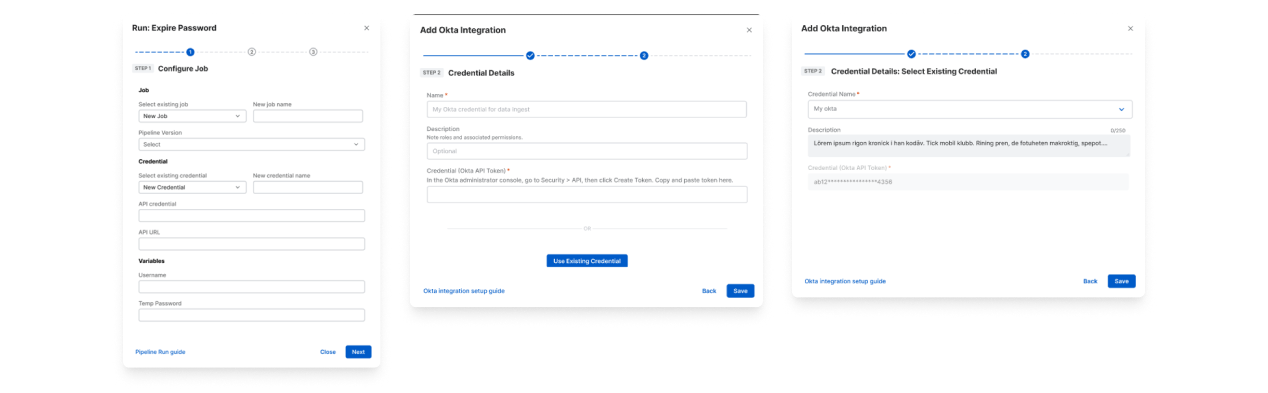
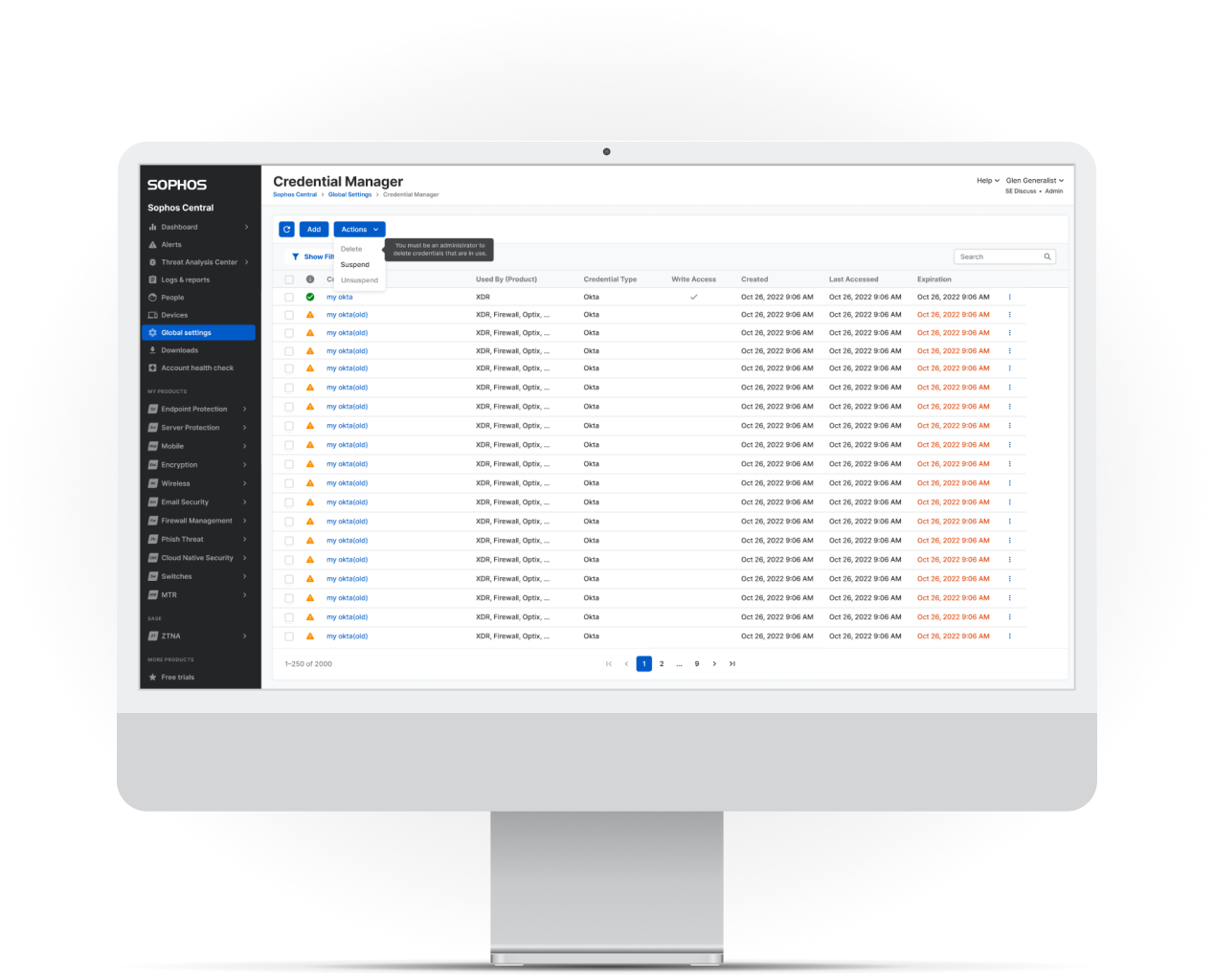
Credentials Too Isolated
Sophos is a large cybersecurity organization with a suite of several security products. The Central Management Console
existed as a hub and single access point, but the platform still relied on a fragmented approach where each
product required separate credential configuration and individual management.
Credentials play a critical role in allowing products to interact with the user's infrastructure and third-party systems.
They include username/password pairs, API keys, tokens, permissions, and other sensitive configuration data that
must be handled securely.
Users frequently recreated the same credentials across multiple products. This redundancy increased operational burden and
introduced security concerns because there was no centralized oversight of where credentials were used.